Version 2.0 of NIST’s Cybersecurity Framework (CSF) was released on February 26th 2024, superseding version 1.1 (2018).
The framework was first released in 2014, primarily aimed at support of US federal and critical infrastructure infosec management. It has in the intervening decade also been used by non-governmental organisations, and the extended framework of CSF2.0 is likely to encourage wider adoption. Its basic structure remains unchanged. It’s a three level hierarchical taxonomy of activities (Function; Category; Subcategory) that drill down from a small number of broad domains of activity to specific outcomes. In CSF1.1 there were five operational functions (Identify; Protect; Detect; Respond; Recover), and the most significant departure in CSF2.0 is the addition of a new (essentially strategic) Govern function.
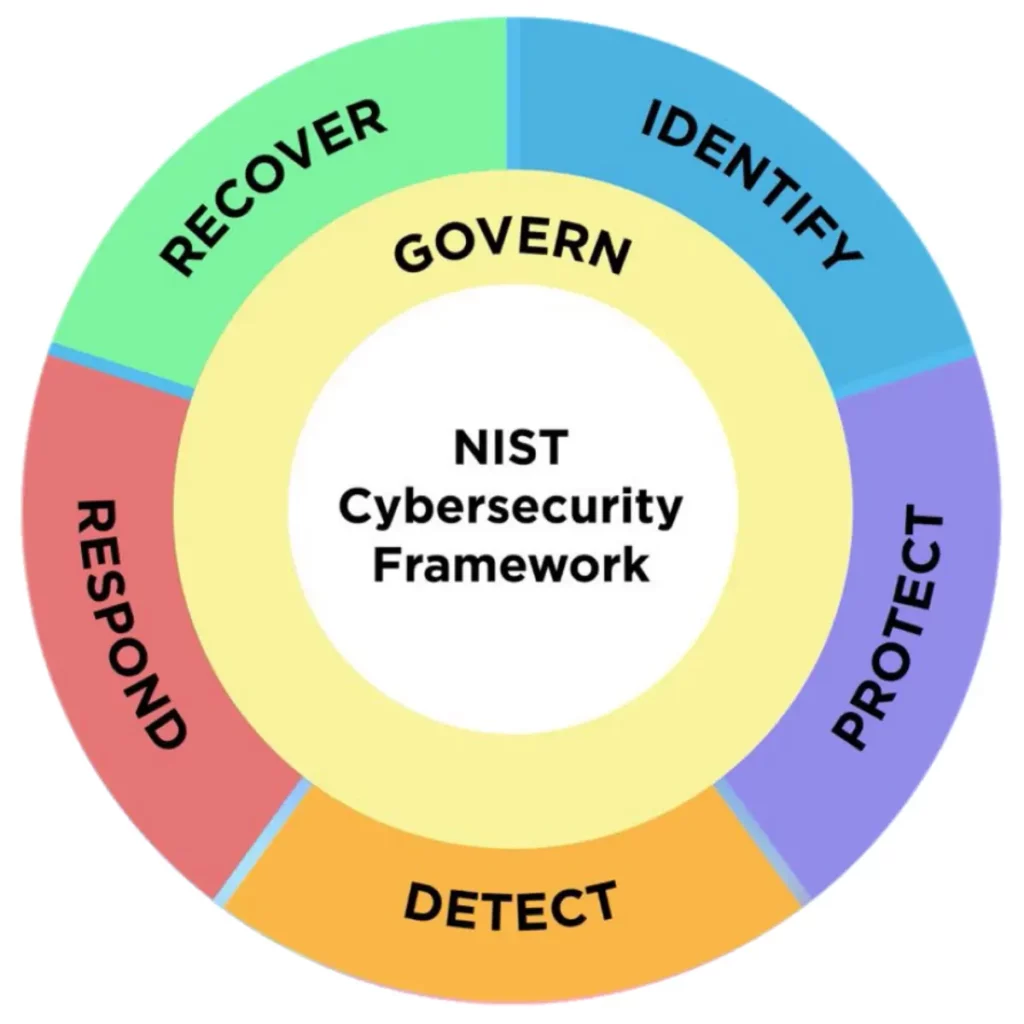
This Govern function has six categories (Organizational Context; Risk Management Strategy; Roles, Responsibilities and Authorities; Policy; Oversight; Cybersecurity Supply Chain Risk Management), the first five of which make perfect sense as elements of governance. They’re really significant extensions of the framework, which has hitherto been too operationally focused. But just as I never understood why the entire CSF1.1 Supply Chain Risk Management (SC) category was stuffed into the Identify function, it’s not really obvious why it’s now landed exclusively in Govern (as Cybersecurity Supply Chain Risk Management). While there are indeed governance elements of supply chain risk management, there are also many primarily operational elements that would fit logically within the other five functions. It’s also not clear why the new SC category has been prefixed with ‘cybersecurity’. The CSF2.0 SC subcategories clearly indicate that the category still refers to the cybersecurity of the supply chain in general, not to some hypothetical ‘cybersecurity supply chain’ so the new category name is a potential source of confusion. Nevertheless, the Govern function is very welcome, finally giving the framework coverage comparable with that of ISO/IEC 27001.
A couple of other apparent anomalies are worth mentioning. The Identify function gains a new category (Improvement) – broadly comparable to ISO/IEC 27001 Clause 10. While this is again a welcome addition in principle, placing it entirely in the Identify function does seem a bit arbitrary. Its headline statement being “Improvements to organizational cybersecurity risk management processes, procedures and activities are identified across all CSF Functions”, I feel that specific aspects of Improvement might have been better distributed among the said functions where relevant, and ideally in rather more detail. It’s also a pity that the CSF1.1 ‘informative references’ to other standards have been omitted from CSF2.0. These were potentially useful when introducing the CSF in organisations where conformity with other standards was already in place.
So why consider the CSF? Not least, one of its strongest elements is its four tier process maturity model, which allows adopters to track their progress towards optimisation of their infosec management. Now that governance is intrinsic to the framework, the maturity model can support continuous improvement of an entire information security management system. Other positives are that it’s presented simply in plain language, it’s focused on outcomes but not prescriptive of processes or paperwork, and both the framework and its support documentation are obtainable free of charge. All these attributes make it accessible for smaller enterprises that might balk at the complexity and cost of going the ISO route. However there is no certification option for organisations – CSF conformity is purely voluntary and self assessed.
Ultimately, notwithstanding the minor issues I’ve mentioned (which are to be expected in the first release of any revised standard, and may be ironed out in time) CSF2.0 has a lot more to offer than CSF1.1. So unless you need a certificate of conformity, it’s well worth considering as a viable practical alternative to ISO/IEC27001, particularly in the SME space.
Author: Mike Barwise, Integrated InfoSec

